Outreach Activity
Outreach Activity
Joint Advisory
Implementing SIEM and SOAR Platforms

On May 27, 2025, the National Center of Incident Readiness and Strategy for Cybersecurity (NISC) co-sealed and published an international document providing guidance on SIEM and SOAR platforms (hereinafter referred to as the "Document"). The Document was authored by the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC). Tentative translations will be released as soon as possible.
The following countries co-sealed the Document and are listed in the Document: Australia, Japan, the United States of America (US), United Kingdom (UK), Canada, New Zealand, Singapore, South Korea, and the Czech Republic.
The Document is intended for organizations that are considering procuring or are already operating SIEM and/or SOAR platforms.It provides definitions, possible advantages, challenges, and best practices for procuring, installing, and maintaining these platforms. The Document is divided into three parts: (1) Executive Guidance, (2) Practitioner Guidance, and (3) Priority Logs for SIEM Ingestion — Practitioner Guidance.
Reference:
Securing edge devices
On February 4, 2025, the National Center of Incident Readiness and Strategy for Cybersecurity (NISC) co-sealed and published an international document entitled "Mitigation strategies for edge devices" (hereinafter referred to as the "Document"). The Document was authored by the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC). Tentative translations will be released as soon as possible.
The following countries co-sealed the Document and are listed in the Document: Australia, Japan, United States of America(US), United Kingdom (UK), Canada, New Zealand, South Korea, Netherlands and Czech Republic.
This document provides seven strategies for risk mitigation in light of the increasing number of attacks targeting edge devices by a number of malicious actors. The NISC co-sealed the Document because it will greatly contribute to the enhancement of Japan's cyber security if Japanese companies, including critical infrastructure providers, refer to the risk mitigation measures for edge devices described in this document.
Reference:
Principles of Operational Technology Cyber Security

On October 2, 2024, the National Center of Incident Readiness and Strategy for Cybersecurity (NISC) co-sealed and published an international document entitled "Principles of operational technology cyber security" (hereinafter referred to as the "Document"). The Document was authored by the Australian Signals Directorate's Australian Cyber Security Centre (ASD's ACSC)
The following nine countries co-sealed the Document and are listed in the Document: Australia, Japan, United States (US), United Kingdom (UK), Canada, New Zealand, Germany, Netherland and South Korea.
This Document is designed to assist critical infrastructure orgnaisations relying on Operational Technology (OT) to provide their vital services. This Document describes six principles that assist organizations make decisions for designing, implementing, and managing OT environments. The NISC co-sealed the Document because the application of these principles to Japanese critical infrastructure organisations will contribute to strengthening cyber security in Japan.
Reference:
Best practices for event logging and threat detection

On August 22, 2024, the National Center of Incident Readiness and Strategy for Cybersecurity co-sealed and published an international guidance entitled "Best practices for event logging and threat detection" (hereinafter referred to as the "Guidance"). The Guidance was prepared by the Australian Cyber Security Centre (ACSC) under the Australian Signals Directorate (ASD).
The following nine countries co-sealed the Guidance and are listed as co-authors: Australia, Japan, United States (US), United Kingdom (UK), Canada, New Zealand, Singapore, South Korea and Netherland.
The Guidance is primarily for senior information technology (IT) decision makers and network operators and is the international best practice for event logging and threat detection. We decided to co-seal it because providing technical measures to combat “living off the land” techniques, which are considered difficult to detect, will contribute to the enhancement of cybersecurity in Japan.The NISC co-sealed the Document because the application of these principles to Japanese critical infrastructure organisations will contribute to strengthening cyber security in Japan.
Reference:
APT40 Advisory PRC MSS tradecraft in action

On July 9,the NISC and the National Police Agency (NPA) co-sealed and published an international advisory entitled "APT40 Advisory PRC MSS Tradecraft in Action" (hereinafter referred to as the "Advisory"). The Advisory was prepared by the Australian Cyber Security Centre (ACSC) under the Australian Signals Directorate (ASD).
Following eight countries co-sealed the Advisory and are listed as co-authoring organizations: Australia, the United States, the United Kingdom, Canada, New Zealand, Germany, South Korea, and Japan.
In Japan, it has been confirmed that Japanese companies had also been targeted by a group conducting cyberattacks known as APT40.
The Advisory analyzes past incidents in Australia by APT40, details their attack techniques as case studies, and provides measures for detecting and mitigating these attacks. Given its contribution to strengthening cybersecurity in Japan, we have decided to co-seal it.
Reference:
Mitigating Cyber Threats with Limited Resources: Guidance for Civil Society

On May 15,the NISC and the National Police Agency jointly co-sealed international guidance for “Mitigating Cyberthreats with Limited Resources: Guidance for Civil Society” (hereinafter referred to as “this guidance”), which is led by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), and are publicizing this guidance.
In addition to U.S. and Japan, Canada, Estonia, Finland, and the United Kingdom co-sealed this guidance and listed their authorities as authoring agencies in this guidance.
In Japan, it has been confirmed that academics, think tanks, journalists, etc., which are referred to in this guidance, are targets of cyberattacks. Given the importance of this guidance, which shows risk mitigation measures to be taken by civil society, Japan has decided to co-seal it.
Reference:
Engaging with Artificial Intelligence

NISC co-sealed a joint publication "Engaging with Artificial Intelligence" led by the Australian Signals Directorate's (ASD's) Australian Cyber Security Centre (ACSC).
This paper helps explain to organizations how to use AI systems securely, summarizes the key threats related to AI systems and suggesting how best to assist AI system users and mitigate these issues.
Reference:
Guidelines for secure AI system development
The Council for Science, Technology and Innovation (CSTI) and NISC co-sealed the “Guidelines for secure AI system development” developed by the UK National Cyber Security Centre (NCSC), the US Cybersecurity and Infrastructure Security Agency (CISA) and 18 international partners.
The guideline helps all stakeholders (including data scientists, developers, managers, decision-makers and risk owners) make informed decisions about how their AI systems should be designed, developed, deployed and operated.
Reference:
Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Security by Design and Default

NISC co-sealed a secure-by-design product compiled by the US Cybersecurity and Infrastructure Security Agency(CISA) and 17 international partners, "Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Secure by Design Software".
This guidance includes the following three principles, namely: Take Ownership of Customer Security Outcomes, Embrace Radical Transparency and Accountability, and Lead From the Top.
This joint guidance gives software manufacturers all the tools they need to demonstrate their commitment to secure by design as well as letting customers evaluate their progress, thus creating a demand signal for secure by design.
This guidance implements the Security by Design concept described in the Cyber Security Strategy of the Japanese government.
Reference:
Cooperation with ASEAN countries
2024 Joint Awareness Raising Activity
As a part of the ASEAN-Japan Cybersecurity Policy Meeting, ASEAN countries and Japanese students were invited to submit an awareness-raising video on cybersecurity.
The videos were submitted to help educate the general public and convey a message to boost awareness of a specific aspect of cybersecurity.
Smishing (Brunei)
Don't let your phone number expire (Cambodia)
Oversharing Might Harm You (Indonesia)
Social networking is dangerous (Japan)
Social media phishing (Lao PDR)
Inside the Mind of a Hacker: A Cybersecurity Journey (Malaysia)
Social Media Safety (Myanmar)
Crafting Strong Passwords for Maximum Protection (Philippines)
Just Fun (Thailand)
The Price of Convenience (Vietnam)
Reference:
2023 Joint Awareness Raising Activity
As a part of the ASEAN-Japan Cybersecurity Policy Meeting, ASEAN countries and Japanese students were invited to submit an awareness-raising video on cybersecurity.
The videos were submitted to help educate the general public and convey a message to boost awareness of a specific aspect of cybersecurity.
Typosquatting (Brunei)
Never use the same password (Cambodia)
Safeguarding kids online (Indonesia)
Journey into Cybersecurity (Japan)
Think before clicking. Life will be safe.(Lao PDR)
Beware of Phishing Scam (Malaysia)
Data Dilemma (Myanmar)
Influencer (Philippines)
Child Bright Safety Life (Thailand)
4Be Safety Online Tip for Children (Vietnam)
Reference:
ASEAN-Japan Performance Report on Cybersecurity Cooperation
ASEAN-Japan Cybersecurity Past and Future
The year 2023 marks the 50th commemorative year (half-centenary) of ASEAN-Japan relations.
The NISC and the cybersecurity agencies of ASEAN member states have participated in the “ASEAN-JAPAN Cybersecurity Policy Meeting” and WG activities since 2009. To further enhance cybersecurity cooperation and build even more capacity in the ASEAN-Japan region, we have summarized the activities and the results in an E-booklet.
Reference:
Cross-sectoral Exercise
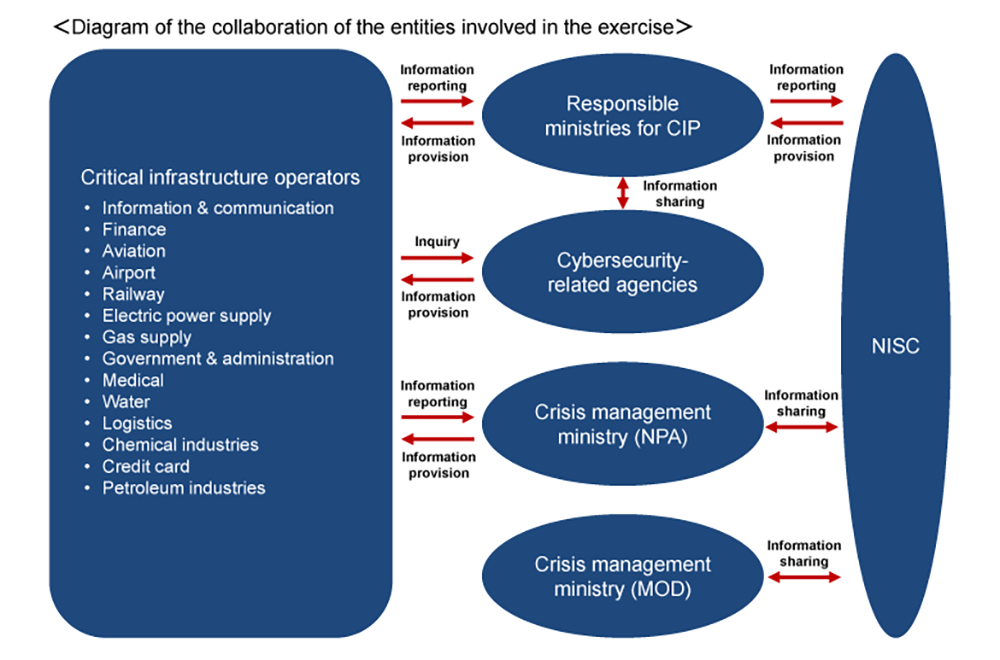
NISC implements a Cross-sectoral Exercise every fiscal year as part of efforts to ensure critical infrastructure services can be provided on an ongoing basis, however adverse the circumstances.
The exercise is conducted in cooperation between NISC and the ministries responsible for critical infrastructure protection (CIP).
1.Objectives
- Verify and improve incident response capabilities across entire organizations
- Contribute to other activities in the Cybersecurity Policy for Critical Infrastructure Protection
2.Overview (FY2023)
- Tabletop exercise (participating either at the meeting site or online from the workplace or home)
- Theme: management involvement and supply-chain measures against ransomware attacks
- Assuming that a critical infrastructure operator suffers a ransomware attack that results in its own systems breaking down, several days may be needed to determine the cause and recover, which will impact on its supply chain.
- Assuming that the incident response involves management decisions like "deciding on the level of critical infrastructure service provision" and "public relations to stakeholders," and practicing cybersecurity as a part of organizational governance.
- Communication among critical infrastructure operators
- Engaging in a roundtable discussion in which critical infrastructure operators exchange opinions with experts at the assembly site prior to the exercise.
3.Participants (FY2023)
- Around 6,100 people from 780 organizations
- Critical infrastructure operators (14 sectors)
- Ministries responsible for (FSA, MIC, MHLW, METI, MLIT)
- Crisis management ministries (NPA, MOD)
- Cybersecurity-related agencies (IPA, JPCERT/CC)

Meeting site of the Cross-sectoral Exercise (FY2023)
PR Video:

